SAFEGUARDING WIRELESS COMMUNICATION NETWORKS WITH CELLULAR-CONNECTED UAVS: A PHYSICAL LAYER SECURITY PERSPECTIVE
Security has not been at the foundation of wireless communications technology development but is becoming increasingly important. By taking into consideration the advantages of UAV technology, including but not limited to their low deployment cost, high maneuverability, strong line of sight (LOS) radio communications links with ground nodes, and ability to operate in dangerous or hostile environments have motivated my research of integrating UAV into terrestrial communication networks for enhancing next-generation wireless network security. I have developed a framework and various algorithms based on the network optimization and learning theory that leverage the 3D movement, power control, and beamforming techniques adopted by the UAVs to enhance the fundamental secrecy performance limits of terrestrial wireless communication under active and passive eavesdropping attacks. The secrecy performance is evaluated through the secrecy rate metric, which is modeled with trajectory, power, scalability, and others. constraints related to the deployment environment, attack type and quantity, and UAVnode capabilities as a non-convex optimization problem with a non-smooth objective function. To address this problem, firstly, an iterative algorithm derived from the block coordinate descent strategy is proposed to optimize the transmission power and UAV trajectory for enhancing the secrecy rate of multiple ground users under multiple eavesdropping attacks to address the search gap of scalability. Motivated by the promising results accomplished, I went one step further to ask the following questions: (1) Can machine learning algorithms be applied to further reduce the complexity and convergence time of the proposed UAV-assisted securer terrestrial wireless networks? (2) Is it possible to enhance the secrecy rate of the network without having channel state information (CSI) of the eavesdroppers to address the research gap in analyzing the practicality of mitigation techniques against eavesdropping attacks? My recent research has demonstrated practical solutions to these research questions. For future research plans regarding this research, I am interested in investigating more scenarios for optimizing the design of the UAV trajectory under a wide range of realistic constraints, such as collision avoidance, and no-fly zone restrictions. Moreover, I am motivated to research the capabilities of the UAV in the 3D space to enable novel end-to-end solutions for enabling wider use of dynamic spectrum-sharing policies. In addition, Theoretical and practical problems at the physical (PHY), medium access control (MAC), and higher layers will be investigated to enhance the fundamentals of communication support for aerial nodes in air corridors while taking into consideration limited UAV energy resources.
TOWARD NEXT-GENERATION OPEN RADIO ACCESS NETWORKS (O-RAN) DEVELOPMENT
The need for transformations from an inflexible and monolithic wireless communication system to a flexible, agile, and disaggregated architecture to support service heterogeneity, coordination among multiple technologies, and rapid on-demand deployments are enabled by the emerging open radio access network (O-RAN). The O-RAN framework provides virtualization, intelligence, and flexibility while defining open interfaces for network innovation. In my research, I strive to explore the capabilities and limitations of the current architecture design, components, and software libraries. My research has focused on identifying the security, latency, real-time control, and testing gaps. Specifically, for security enhancements of the O-RAN, I am planning to investigate the potential of mutual authentication for verifying access to the O-RAN system and preventing malicious applications and components, mechanisms enabling the trusted implementation of xApps and AI models, and cryptography with secure key management, including key generation, storage, rotation, and revocation as a future research direction. Moreover, my research also includes prototyping a small-scale software-defined radio (SDR)testbed featuring an open-source O-RAN based 5G Non-Standalone (NSA) communication system that can interact with the near-real-time (near-RT) RAN intelligent controller (RIC) of the O-RANarchitecture through standard interfaces. The research focuses on the O-RAN E2 interface interactions and outlines the procedure to enable a RAN system with E2 capabilities. Other future research directions include the design of data-driven intelligent solutions and efficient control loops for different O-RAN deployments such as non-terrestrial and spectrum sharing.
UAVS WITH RECONFIGURABLE INTELLIGENT SURFACES: APPLICATIONS, CHALLENGES, AND OPPORTUNITIES
The reconfigurable intelligent surface (RIS) is a candidate 6G technology that enables new wireless transmission patterns by controlling the signal propagation and the communications channel. TheRIS facilitates reflection of the incident radio waves, which can be controlled in real-time to shape the electromagnetic signal and steer it in the desired direction. Therefore, to further expand my previous UAV research at the physical layer, I have proposed the joint integration of UAV and RIS under a novel framework called aerial RIS (ARIS). With such direction, my research has focused on improving the achievable data rates of ground users in different scenarios by employing the ARIS to support terrestrial wireless networks. Optimization of the transmission data rates in such cases are NP-hard under the constraints of UAV trajectory, power, and phaseshifts. Therefore, I have proposed an iterative mathematical tool and RL algorithm to solve these optimization problems by jointly designing the reflection coefficients of the RIS passive elements, active beamforming of the transmitter, and UAV trajectory. The obtained results from this research open many research directions to be investigated in the future, such as applying this solution for improving the secrecy rate of ground users while trying to disrupt the performance of attackers by arbitrarily controlling the attacker’s channel. Other future directions for both ground and aerial RIS include as the interaction between various RISs, doppler resilience of phase-shifts, direct/indirect path analysis, and signal processing. In addition to expanding the scope of my research to enable cutting-edge contributions to emerging RIS for integrated sensing, computing, and localization in different resource-restricted wireless communication networks such as IoT, internet-of-everything (IoE), UAV, and vehicle-to-everything (V2X).
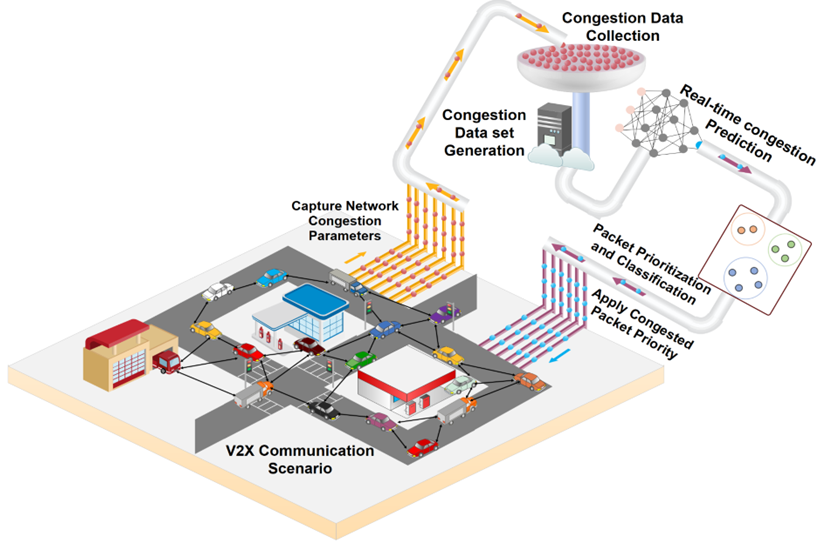
Proactive Congestion Management for Internet of Vehicle Networks
Vehicle-to-everything (V2X) networks support a variety of safety, entertainment, and commercial applications. This is realized by applying the principles of the Internet of Vehicles (IoV) to facilitate connectivity among vehicles and between vehicles and roadside units (RSUs). Network congestion management is essential for IoVs and it represents a significant concern for the economic, environmental, and industrial sectors. This is due to its impact on several pressing problems, such as improving the efficiency of transportation systems and providing reliable communication among vehicles for the timely delivery of safety-critical packets. This research introduces a framework for proactive congestion management for IoV networks. We generate congestion scenarios and a data set to predict the congestion using LSTM. The V2X packet congestion dataset is developed using SUMO with modified version of NS3 tools for forecasting IoV network congestion. Additionally, the recurrent neural network is employed for clustering/prioritizing packets.